UPDATE July 19, 2014: Espionage 3.6 is out! Go get it! 🙂
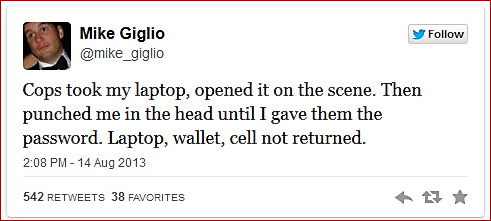
Plausible deniability (in cryptography) refers to methods of protecting users (and their encrypted data) from so-called “gun-to-the-head scenarios”:
Any situation that involves some type of coercion stands to benefit from plausible deniability. Although unlikely, some users may find themselves threatened into giving up their encryption keys through physical force, or by the threat of loss of freedom (examples here, here, and here).
It is quite unfortunate, therefore, that it’s possible to count on one hand the number of data security applications that attempt to do anything to address this issue.
Data security does not stop at encryption
We believe that “security” which protects users in some circumstances (but not others), from some adversaries (but not all), is inferior to security that has no exceptions.
When we designed Espionage 3, we decided to focus on plausible deniability as a core feature. It was never an afterthought. We discovered, that In order to do plausible deniability correctly we had to build the entire app around the concept.
When we released Espionage 3 in 2012, it was (to our knowledge) the first data security app to sport not one but two types of plausible deniability:
- Unlimited isolated master passwords, each protecting a unique Folder Set.
- Multi-faced folders that can show different data depending on whether or not they are locked, and which master password was used to unlock them. This resulted in some fascinating possibilities (like having different versions of your email).
Plausible deniability is Hard
An operating system like OS X has thousands of moving parts, many of which are out of the control of users and third-party developers (like us). This makes hiding the existence of encrypted data a significant challenge.
For example, try observing your system’s primary log file by opening the Console application (located in /Applications/Utilities/Console.app ) while you lock and unlock your encrypted folders. Depending on your version of OS X, you’ll see different types of information about your encrypted folders logged (like the path to the folder).
It is close to impossible to prevent this type of information leakage because it is created by applications and system components that are out of Espionage’s control (and shouldn’t be under its control). It is possible, however, to mitigate it by various means:
- Periodically scrubbing your log files using utilities like OnyX.
- By creating Folder Sets with different data using the same mountpoint
- Etc.
One piece of data leakage, however, cannot be mitigated by users, and that is the number of user-created Folder Sets in Espionage’s database. This, however, is something we can fix (and do fix) in Espionage 3.6. We’d like to thank user tzugo for bringing this issue to our attention.
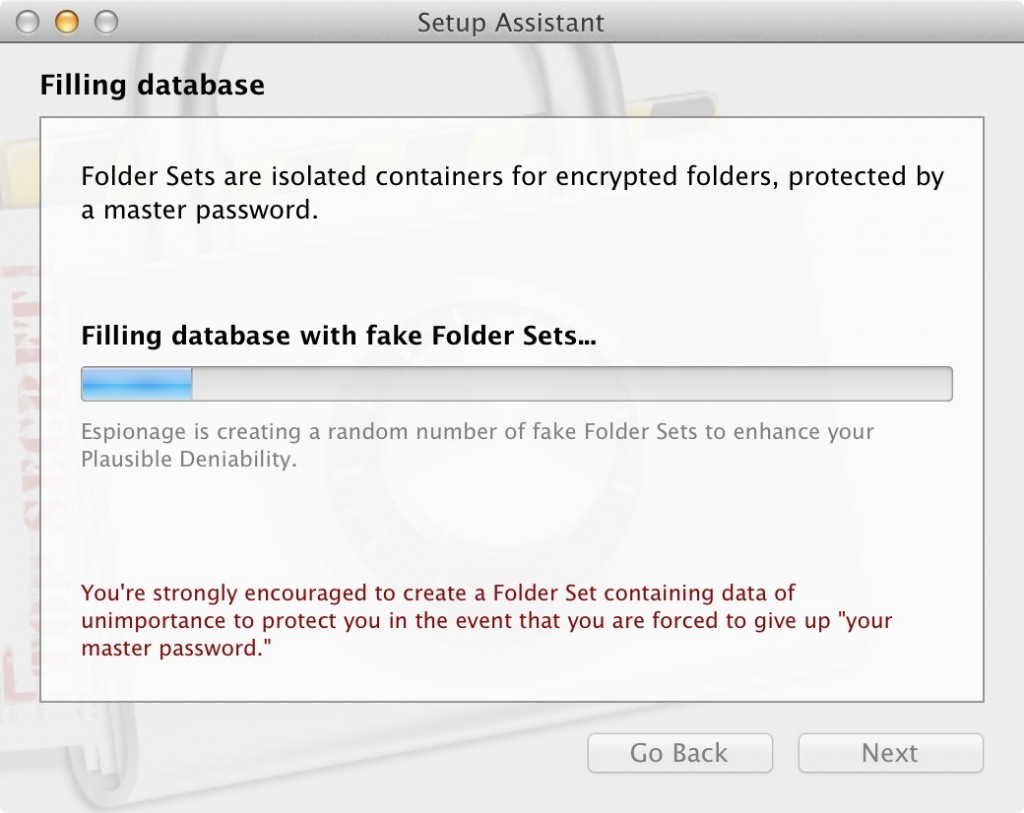
Fake Folder Sets are coming in Espionage 3.6
By having Espionage create a random number of fake Folder Sets, and then creating a user-specified-but-quickly-forgotten number of encrypted sparsebundles (each with a random number of files containing random data), we are able to restore the plausible deniability impacted by this information leakage.
Now, it still remains possible to check how many Folder Sets exist in Espionage’s database, but that information does not reveal the actual number of user-created Folder Sets! They might have one, five—even zero “real” Folder Sets! 🙂
The number of encrypted disk images on a user’s computer, also, does not give away the number of real encrypted disk images that the user has. It is even possible that none of the encrypted disk images contain any meaningful or user-created data (those might be on an external drive, for example).
When users update to Espionage 3.6 (or install anew), they will be taken through a setup assistant that creates all of these faux Folder Sets and disk images. Here’s a sneak peak at what it looks like:
Important notes and considerations
Because Espionage 3.6 is a significant update that makes many changes to Espionage’s database, Espionage will backup the database prior to running the setup assistant and add a “-v2migration” suffix to it. It will be placed in the standard database backups folder, located here:
/Users/[your username]/Library/Application Support/com.taoeffect.Espionage3/Backups
Note that these old backup databases can be used to compromise your plausible deniability (because they show an accurate count of the Folder Sets you created).
Once the assistant finishes successfully, and you’ve verified that you can unlock all your Folder Sets and encrypted folders, you may then delete all of the old backups in that folder to restore your plausible deniability.
Also: starting with version 3.6, we will be signing all Espionage releases with our public key. Espionage 3.6 will also include a pinned 4096-bit public DSA signing key for Sparkle updates (instead of relying solely on HTTPS for securing updates).
Remember: plausible deniability is ultimately *YOUR* responsibility!
Espionage can only do so much for you. It is ultimately *your* responsibility to create convincing enough Folder Set(s) to protect you from gun-to-the-head-scenarios.
Most users won’t need to worry about this at all. For some, however, failure to take due diligence in this regard can result in undesirable consequences. If you think this applies to you, please make sure to do your homework!
Espionage 3.6 is currently getting its finishing touches and final testing. As per usual, it will be released “when it’s ready.” 🙂
Loved to know this software and have put on my shopping list! Thanks for developing this Wonderful Application =)